System Configuration ModuleThis module allows you to view system settings and to make changes to preferences, enabled features and serial keys. You access the module as a System Administrator using the System Configuration link on the dashboard. 
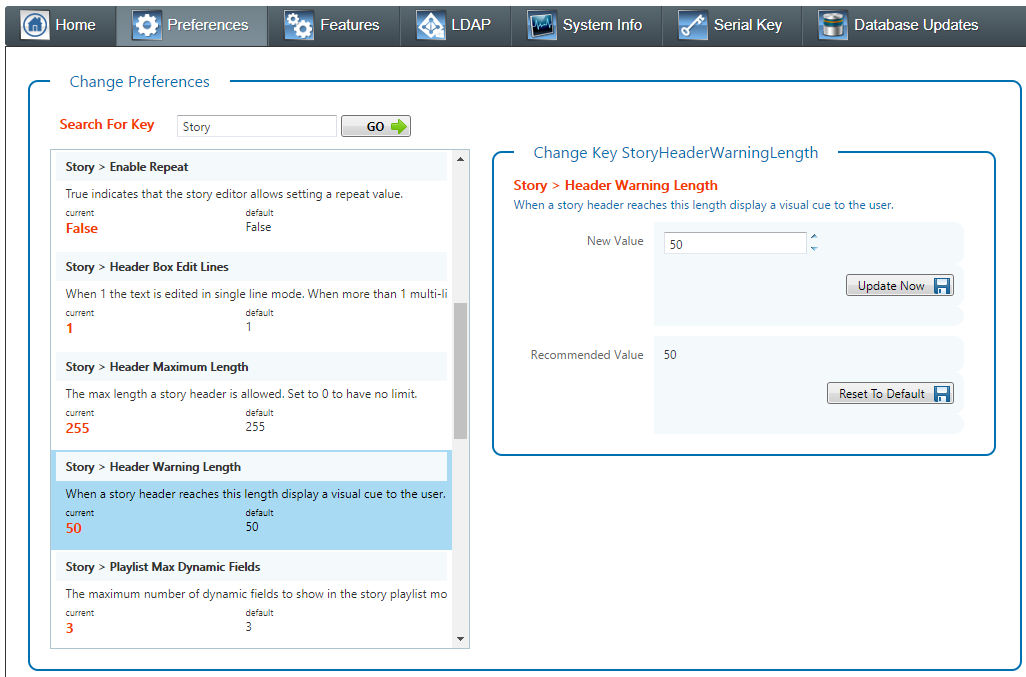
PreferencesThe preferences section allows you to control a plethora of customization options that affect the way Chameleon behaves. You can set the warning length for story headers and bodies or disable the use of dynamic fields.Or set the temperature scale or wind speed units. Also set many default values used when creating new topics. Changes to the preference values will take effect when the change is saved. In the screenshot below you can see - the list was filtered to show only preferences related to Story
- the selected preference setting is for the Story Header Warning Length
- the value can be changed and saved
- the value can be reset to the default value using the reset button
System InfoThe system info section provides a summary of information about the browser, installed components and culture settings. This is a report only - no changes can be made here. 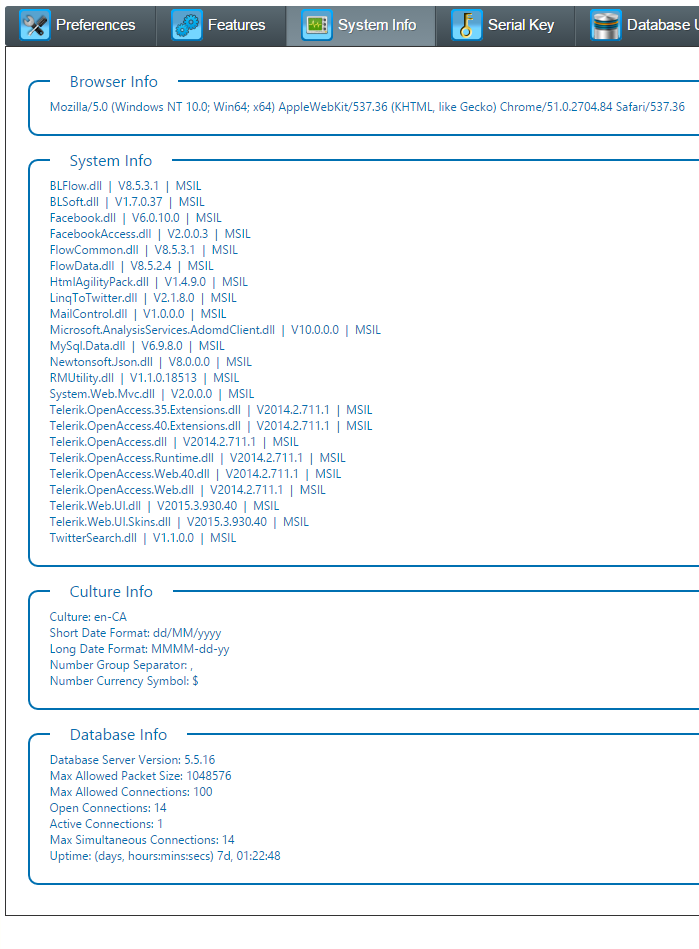
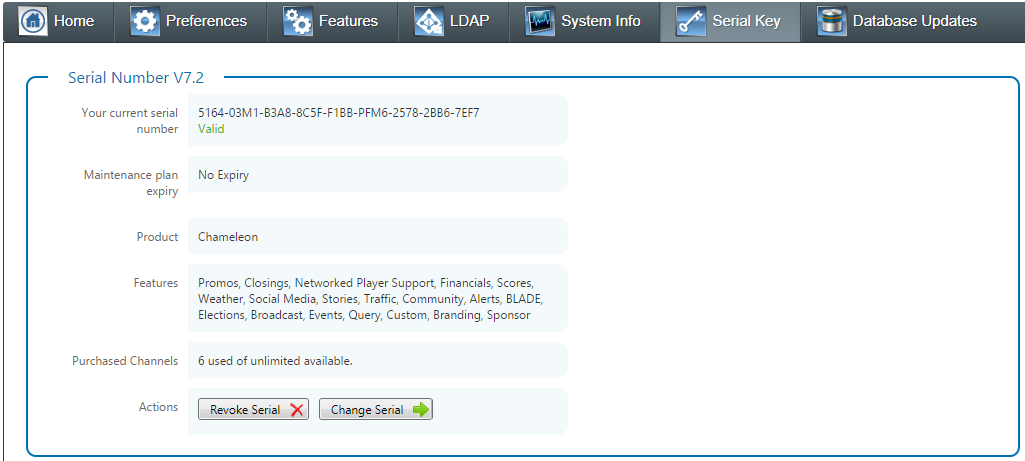
The culture info represents the server settings that are used when displaying content in Chameleon To change these you must change the corresponding settings on the web server that is hosting the Chameleon application. Serial KeyThe serial key section allows you to view and change the serial associated with the instance of Chameleon. The serial keys control which features of your product can be enabled for use. It displays: - your current serial number
- and indicates if it is valid
- Expiry date
- some serials are created for demo or trial use and will expire while others have no expiry
- Product
- this identifies which product the key enables - Example: Chameleon, Tick-it, etc.
- Features
- this is a list of available features that you are licensed to use.
FeaturesThis section allows you to control which of the features are enabled for use in Chameleon. Disabled features do not show: - on the home page dashboard
- in the BLADE module
You would choose to disable modules if your serial gives you more features than you wish to currently use. If you decide you would like to use them you can always re-enable them here. After making your changes press the Save button. A popup message will confirm when the changes are saved. 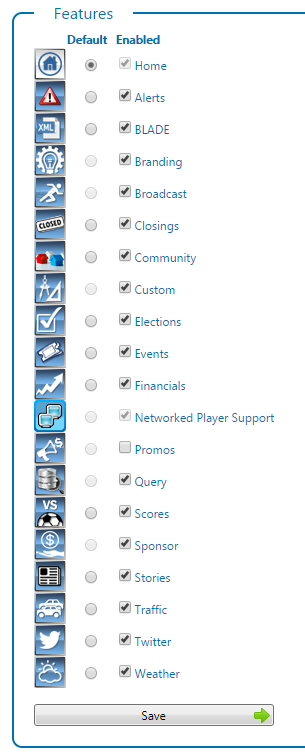
This features section was added in version 6.10.4.2 Database MaintenanceThis section provides a glimpse into the update status of the system. 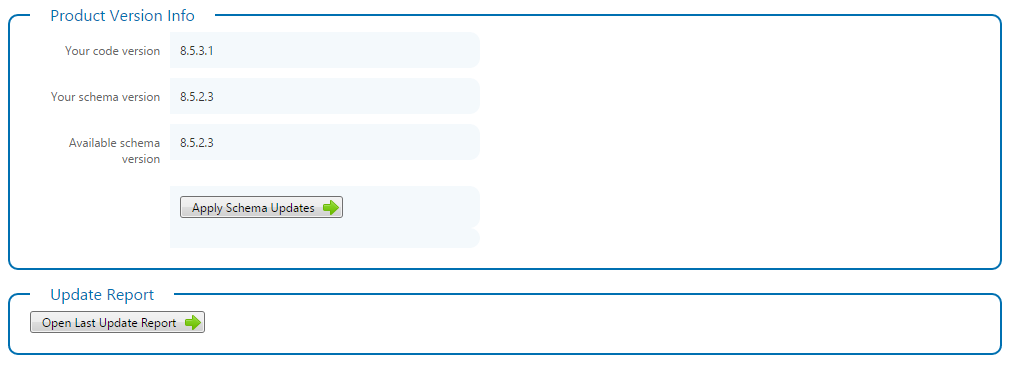
Google Login| Note |
|---|
| Available in version 8.10.2.4 |
You can enable individual users to login using their existing google account instead of using separate password stored in Flow. Enable in System PreferencesTo enable this you must set the appropriate System Preference keys. - Google > Login
- Google > Client Id
- You can aquire acquire a google client ID by registering a Google API Console project
- Be sure to set the Authorized JavaScript origins to match the URLs you will be accessing your instance of Chameleon with.
Assign Users to Google LoginFollow instructions here. LDAP| Note |
|---|
| First edition available in version 8.9.4.3 Support for a search user enabling additional user attributes such as sAMAccountName attribute where added in 9.5.4.5. Improved Active Directory support available in 9.6.2.2 |
You can enable individual users to login using an LDAP-compatible directory username and password instead of having a separate password in Flow while at the same time allowing other users to login using Flow defined credentials. Good to know: - You still need to create an account in Flow for each user to be able to assign privileges in Flow. These users can be imported from an CSV formatted file. See this Import Users page for more information.
- The username must match their username in the LDAP directory.
- When they login Flow will check the password against the LDAP-compatible directory instead of the Chameleon database.
- You can test your connection settings even before you save or enable them.
- See the Connection Testing section for more info below...
- Use of LDAP must be enabled on each user record it will be used with as well as turning on the main "Allow LDAP Login" on the LDAP config page.
If you have existing users with passwords that are already in use - you can still switch to LDAP. Activating LDAP support will not remove those existing passwords. LDAP Setting AccessYou access the LDAP settings in the Configuration module. This module can be accessed by a logged in System Administrator or before login by accessing the password protected configuration page directly using a Config url for your installation in the format such as https://chameleon.blcloud.net/Config/ This could allow you to access the LDAP settings if needed without using an LDAP based user login first. LDAP ConfigurationThe individual settings required are also documented inline on the configuration page. In order to connect you'll need to be able to specify: | Setting | Comments |
|---|
| Host Name | The host name of your directory server. Examples: | | Port | The port on which your directory server is listening. Examples: | | Timeout | The number of seconds to wait for a result from an LDAP request before timing out. | | Search User DN and Password | The distinguishedName (DN) of the user to login with to perform user searches.
This user needs to only be granted view/search privileges. It does not update the directory. Example: cn=read-only-admin,dc=example,dc=com Added in build 9.5.4.5 These fields aren't used if you have a situation where the user DN can be directly determined via a concatenation of User Attribute, User RDN, Base DN. | Search Filter | The filter used when searching for users in the directory. Examples: - For LDAPv3: (objectClass=inetOrgPerson)
- For AD: (objectCategory=person)(objectClass=user)(!sAMAccountType=805306370)
| | Base DN | The root distinguished name (DN) to use when running queries against the directory server. Examples: - o=example,c=com
- cn=users,dc=ad,dc=example,dc=com
- For Microsoft Active Directory, specify the base DN in the following format: dc=domain1,dc=local. You will need to replace the domain1 and local for your specific configuration. Microsoft Server provides a tool called ldp.exe which is useful for finding out and configuring the LDAP structure of your server.
| Additional User RDN (multiple) | This value is used in addition to the base DN when searching and loading users. If no value is supplied, the application will build the lookup path using only the base DN. Example: You can define multiple User DNs and assign each a friendly name that is selected when setting up the user in the user module. | | User Attribute | The attribute of an LDAP user object that specifies the login name of the user. Examples: |
Connection TestingYou can test your connection settings before you enable them. To do so - fill in the all the configuration settings. (You don't even have to save the settings - the test buttons use the values entered into the form - not the saved values) Then you have two options for testing the connection setting: - Test if we are able to do a basic connect to the server
- Press the Test Connection button after saving your configuration settings
- NOTE: this will not work if your server doesn't support anonymous binds (unauthenticated access).
- it may also work for a server in your domain but then not work from a server outside its domain.
- Test if we are able to connect to the server using the defined search user.
- Press the Test Search User button after entering the required search user information.
- NOTE: this may work even if the above basic test connect does not because it is using the search user id and password to authenticate.
- Test if a given userid/pwd will successfully authenticate.
- Enter the userid and password and press the Test Login button.
Connection DebuggingTo help with debugging why a login test might not work you can enable a preference key to enable additional tracing. In the preferences module search for "tracing". You will find an LDAP Tracing option. Set this to True to enable it. When the tracing option is enabled you can view the messages in an audit report. From the dashboard/home page look for the Reports group and then select the Audit Log. On the Audit report page, change the Report Type select list to be Login Audit Events. 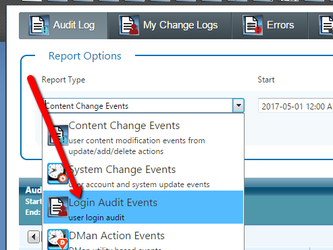
Report items to look for: - is the correct host and port values being passed in?
- is the search filter criteria correct?
- if it found a user did it successfully extract the user DN?
NotesIf using the cn user attribute as the login name then you may be able to use the LDAP authentication without the need for a search user. The application concatenates the user attribute and value to the additional user dn and the base dn to build the complete user distinguishedName (DN). If the using an alternate attribute that is not part of the defined user distinguishedName - then a search user is required to allow the app to search for the user by using the alternate attribute (eg. sAMAccountName) and then grab the user distinguishedName from the user record. Either way: the application then passes the unique DN and password to the LDAP server to check if the combination is valid and if so they are allowed to login. Good to Know - You still need to create an account in Flow for each user to be able to assign privileges in Flow.
- The username must match their username in the LDAP directory.
- When they login Flow will check the password against the LDAP-compatible directory instead of the Chameleon database.
- You can test your connection settings even before you save or enable them.
- See the Connection Testing section for more info above...
- Use of LDAP must be enabled on each user record it will be used with as well as turning on the main "Allow LDAP Login" on the LDAP config page.
|